What Is IoT | What Is IoT Technology And How It Works | Internet Of Things Explained | Simplilearn
This video explores the concept of the Internet of Things (IoT), its benefits, and its applications in various industries. The IoT refers to connecting any device to the internet...
Read moreWindows 10 Hardening
This video explores Windows 10 security enhancements through targeted setting adjustments that boost protection without hindering system performance. It highlights the critical role of aligning security measures with specific...
Read moreWhat Is Raspberry Pi? | Raspberry Pi Explained | Raspberry Pi Tutorial for Beginners | Simplilearn
The Raspberry Pi is a small, low-cost computer that connects to a monitor or TV and uses a conventional keyboard and mouse. It can perform tasks such as accessing...
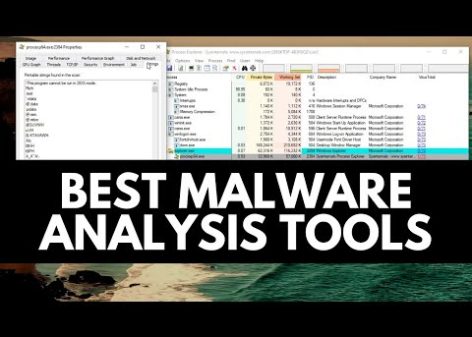
Read moreBest Malware Analysis Tools | Learn Malware Analysis
Here is a 5-sentence video description: This video covers some of the best malware analysis tools used for static and dynamic analysis. The tools discussed include Process Explorer,...
Read moreThe host discusses various topics related to cyber security, including the importance of motivation and finding passion in one's work. He also talks about the future of pentesting with...
Read moreIoT Internet of Things | What Is IoT and How It Works? | IoT Explained in 5 Minutes | Simplilearn
The internet revolution has evolved through three major phases: personal computers, mobile devices, and now the Internet of Things (IoT). IoT connects everyday devices to the internet, reshaping how...
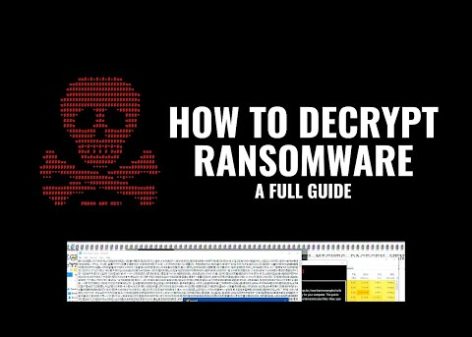
Read moreHow to Decrypt Ransomware: A full guide
- This video explores the options available to decrypt files after a ransomware attack. - It discusses how some ransomware variants may have flaws in their encryption algorithm,...
Read moreThreat Hunting Tutorial: Introduction
This video provides an overview of threat hunting, a topic that can be approached in three different ways. The first type involves looking for threats within an organization's systems,...
Read more