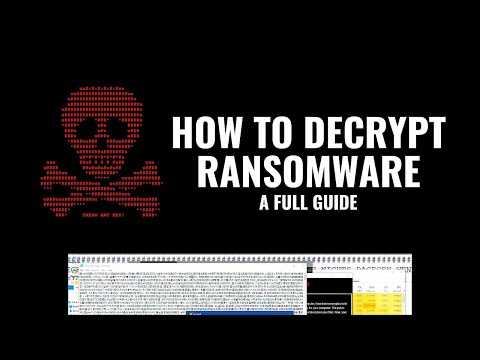
- This video explores the options available to decrypt files after a ransomware attack. - It discusses how some ransomware variants may have flaws in their encryption algorithm, making it possible to recover the key without paying the ransom. - The video also covers the use of brute force methods and the importance of prevention in protecting against ransomware attacks. - Additionally, it highlights the limitations of these methods and the potential for scams that promise easy solutions. - By understanding the science behind ransomware decryption, viewers can make informed decisions about their data protection strategies.
Introduction The video discusses how to decrypt files after a ransomware attack, specifically focusing on the Jigsaw variant. Key Facts 1. Encryption basics: Encryption is the process of encoding data in a way that can only be understood by someone with the decryption key. 2. Ransomware and keys: Ransomware often claims there’s no way to decrypt files without paying the ransom, but this isn’t always true. 3. Static keys: Some ransomware uses static keys, which are hardcoded within the executable, making it possible to decrypt files if you have the key. 4. Brute force decryption: Brute force decryption involves trying every combination of characters that could represent the key, but this is computationally intensive and often impractical. 5. Flaws in implementation: Ransomware developers may implement encryption algorithms securely, but their implementation may contain flaws, such as predictable random number generation